The point of this post is to help those that can’t have 2 NIC on 2 separated not routable subnets. I have already encountered some customers whose security team stated that it was technically impossible to deploy an additional subnet on their current security/network infrastructure.
Many of you know that Lync Edge Requirements have the following statement:
The internal and external subnets must not be routable to each other.
In http://technet.microsoft.com/library/gg412847.aspx
To meet this requirement we need two subnets on our DMZ, as showed in the following example:
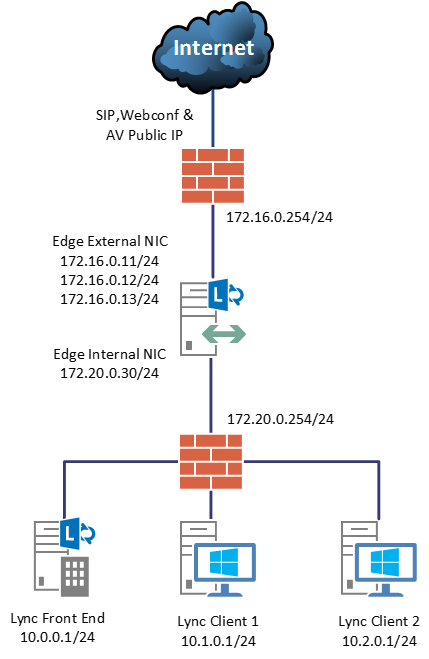
Since we can only have one default gateway, the routes to the internal address should look like this:
route ADD 10.0.0.0 MASK 255.255.255.0 172.20.0.254 METRIC 1
route ADD 10.1.0.0 MASK 255.255.255.0 172.20.0.254 METRIC 1
route ADD 10.2.0.0 MASK 255.255.255.0 172.20.0.254 METRIC 1
What about those deployments that only have one subnet for the Lync Edge Network Interfaces?
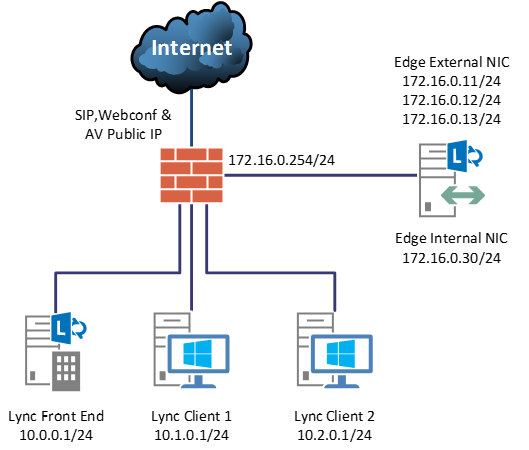
In this example, we have 2 interfaces with the same gateway. It’s common to create a route as in the previous example — although this can work in some cases, what can happen is that Lync Edge will use External NIC to reach internal address.
Firewall will block all communications from the external NIC to internal address. Also, Lync Front End isn’t expecting External NIC to reach it.
The workaround is to specify how Lync Edge NIC should be used to reach internal address. This can be achieved by following 2 simple steps:
Step 1 – Find Edge Internal interface number
Command Prompt
First we need to know the internal interface name:
ipconfig /all
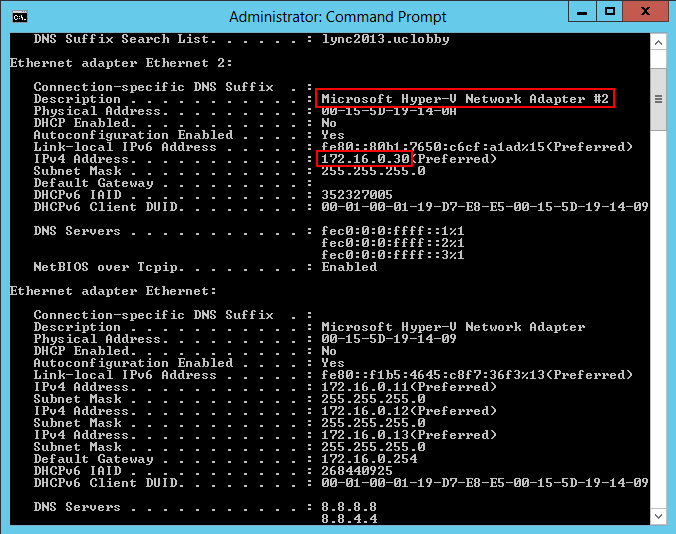
Note: We already know that 172.16.0.30 is the internal interface IP address.
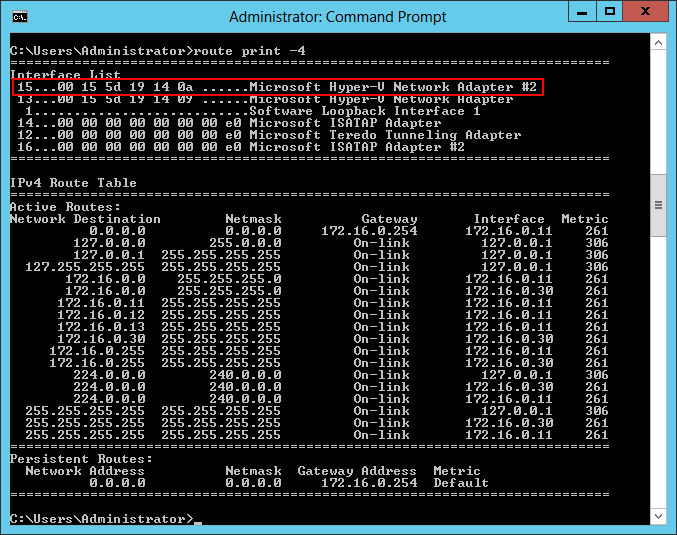
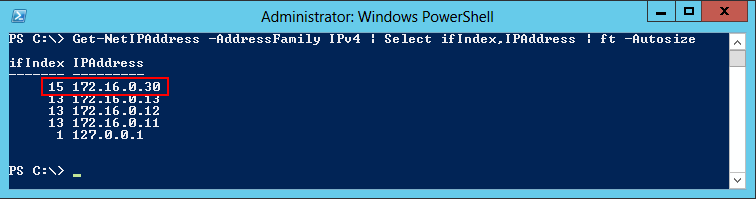
After getting the interface name, let’s get the Interface Index — 15 in this case:
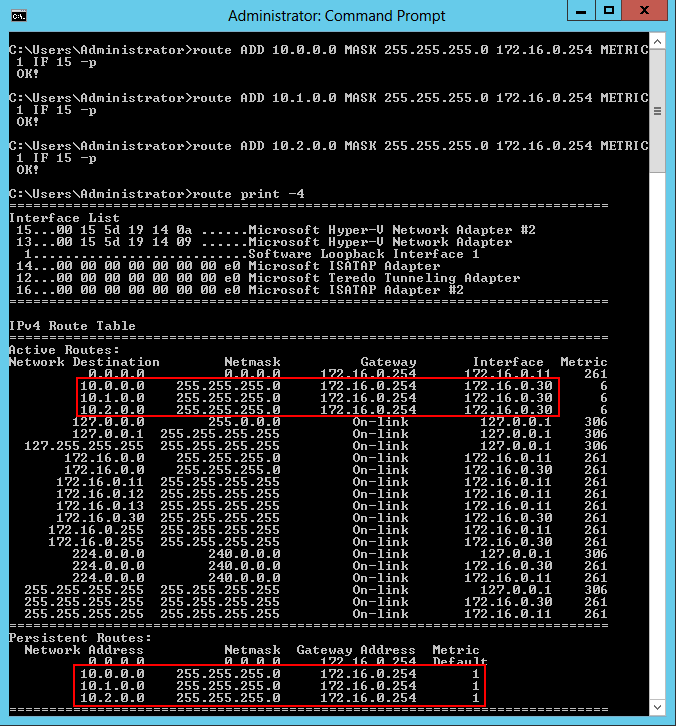
route print -4
PowerShell (only in Windows Server 2012/2012R2)
The following Cmdlet — which is only available on Windows 8/8.1, Server 2012/2012R2 — displays the Interface Index more quickly than the Command Prompt method.
Get-NetIPAddress -AddressFamily IPv4 | Select ifIndex,IPAddress | ft -Autosize
Step 2 – Create the proper routes in the IP routing table
Now all we need to do is create the routes that specify the Interface Index:
Command Prompt
route ADD 10.0.0.0 MASK 255.255.255.0 172.16.0.254 METRIC 1 IF 15 -p
route ADD 10.1.0.0 MASK 255.255.255.0 172.16.0.254 METRIC 1 IF 15 -p
route ADD 10.2.0.0 MASK 255.255.255.0 172.16.0.254 METRIC 1 IF 15 -p
PowerShell (only in Windows Server 2012/2012R2)
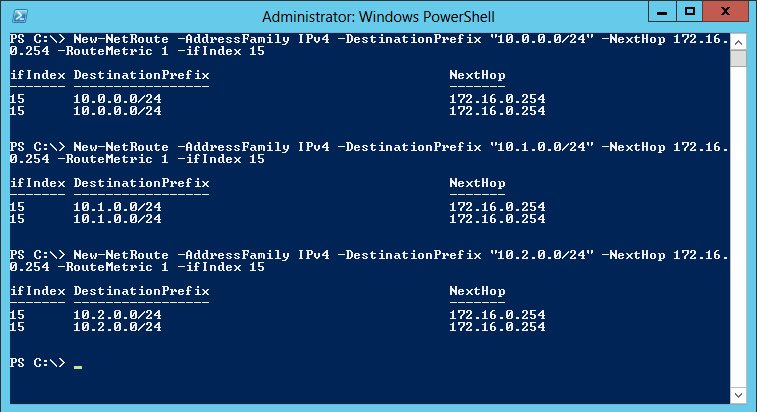
New-NetRoute -AddressFamily IPv4 -DestinationPrefix “10.0.0.0/24” -NextHop 172.16.0.254 -RouteMetric 1 -ifIndex 15
New-NetRoute -AddressFamily IPv4 -DestinationPrefix “10.1.0.0/24” -NextHop 172.16.0.254 -RouteMetric 1 -ifIndex 15
New-NetRoute -AddressFamily IPv4 -DestinationPrefix “10.2.0.0/24” -NextHop 172.16.0.254 -RouteMetric 1 -ifIndex 15
After these changes, the Lync Edge will use internal NIC for all communications to the Front End(s) and Clients. Do remember this workaround should only be used if you can’t have 2 not routable subnets on Lync Edge Server.
TIP: If you want, you can create routes to all possible internal addresses, as long as your company follows what is described in RFC1918 regarding private IP address:
Command Prompt
route ADD 10.0.0.0 MASK 255.0.0.0 172.16.0.254 METRIC 1 IF 15 -p
route ADD 172.16.0.0 MASK 255.240.0.0 172.16.0.254 METRIC 1 IF 15 -p
route ADD 192.168.0.0 MASK 255.255.0.0 172.16.0.254 METRIC 1 IF 15 -p
PowerShell (only in Windows Server 2012/2012R2)
New-NetRoute -AddressFamily IPv4 -DestinationPrefix “10.0.0.0/8” -NextHop 172.16.0.254 -RouteMetric 1 -ifIndex 15
New-NetRoute -AddressFamily IPv4 -DestinationPrefix “172.16.0.0/12” -NextHop 172.16.0.254 -RouteMetric 1 -ifIndex 15
New-NetRoute -AddressFamily IPv4 -DestinationPrefix “192.168.0.0/16” -NextHop 172.16.0.254 -RouteMetric 1 -ifIndex 15