Recently, I received an e-mail from GoDaddy asking to renew older certificates which were signed using SHA-1 algorithm because:
Google® is making a shift in their Chrome™ Web browser to phase out any SSL certificates which use an old encryption algorithm (SHA-1) and expire after Dec. 31, 2015
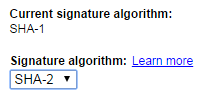
By default, all new or recently renewed certificates should use SHA-2 algorithm:
Regarding Lync environments, this change will only affect users that use Chrome to access Lync Web Services, such as join/schedule meeting and accessing DialIn conference settings. A good thing is that Lync Server supports both algorithms:
Lync Server 2013
All certificates must be signed using a signing algorithm supported by the operating system. Lync Server 2013 supports the SHA-1 and SHA-2 suite of digest sizes (224, 256, 384 and 512-bit)
in Certificate infrastructure requirements for Lync Server 2013
Lync Server 2010
Lync Server 2010 support includes support for SHA-256 certificates for connections from clients running the Windows Vista, Windows Server 2008, Windows Server 2008 R2, and Windows 7 operating systems, in addition to Lync 2010 Phone Edition. To support external access using SHA-256, the external certificate is issued by a public CA using SHA-256.
in Configuring Certificates for Standard Edition Servers
Note: I only found reference to SHA-2 in Lync Server 2010 Standard Edition TechNet.
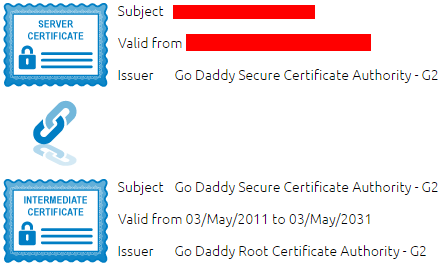
When the certificate is ready, GoDaddy allows you to download the certificate and the Intermediate CA certificates. The P7B file includes two Intermediate CA certificates:
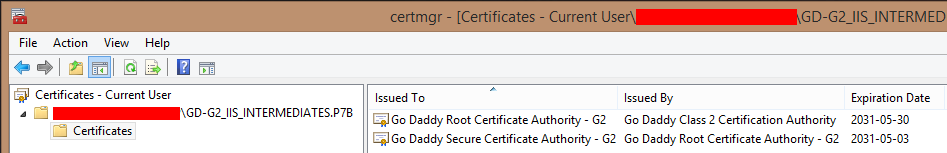
This doesn’t mean that Go Daddy Root Certificate Authority – G2 certificate isn’t valid any more, but that GoDaddy is using cross-signed certificates.
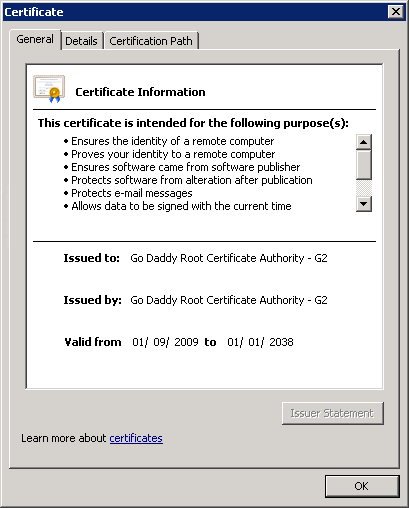
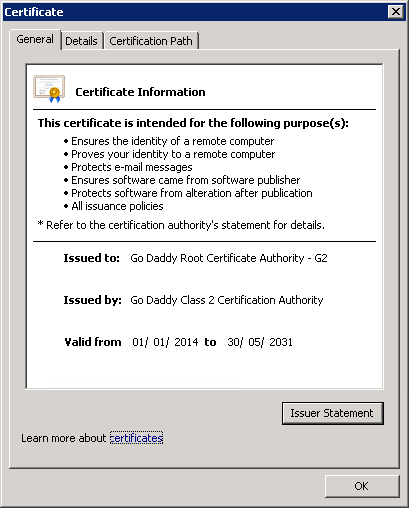
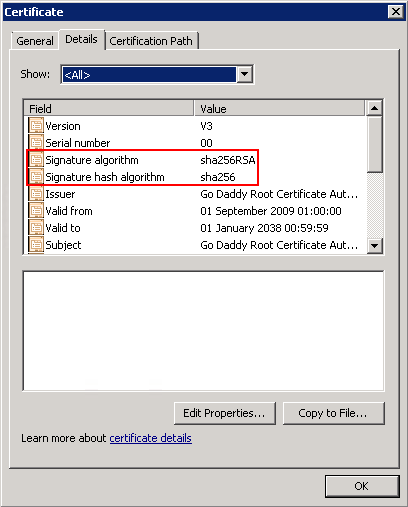
The difference between these two certification chains is that Go Daddy Class 2 Certification Authority uses SHA-1, while Go Daddy Root Certificate Authority – G2 uses SHA-2. We can check which algorithm was used to sign our certificate in the Certificate->Details tab:
Go Daddy Class 2 Certification Authority

Go Daddy Root Certificate Authority – G2
We can test this in a Lab environment – the first step is to install the Intermediate Go Daddy Root Certificate Authority – G2 certificate. Then we need to disable the Go Daddy Root Certificate Authority – G2 certificate, select the certificate, and then right click and open Properties:
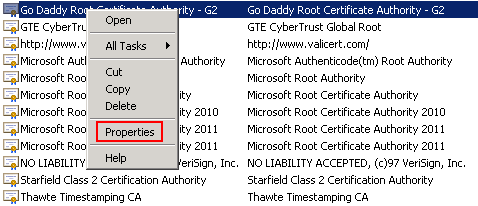
In the properties windows, select Disable all purposes for this certificate:
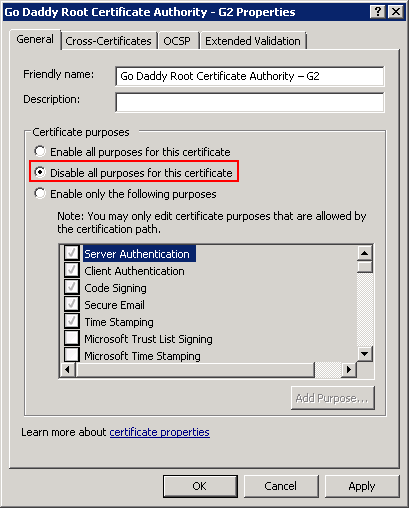
After disabling the certificate, I recommend to reboot the server.
Finally, to check the chain, open the certificate and then select Certification Path:

In case you only disabled the Go Daddy Root Certificate Authority – G2 certificate and didn’t install the Intermediate one, you will get a warning:
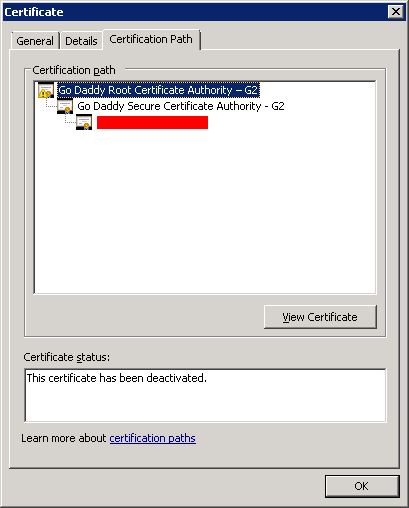
For reference, here is the original chain:

We can also use the DigiCert – SSL Certificate Checker (https://www.digicert.com/help/):
Go Daddy Class 2 Certification Authority as Root CA

Go Daddy Root Certificate Authority – G2 as Root CA