It is really important to regularly check the Event Viewer for Warnings/Errors (or to use System Center Operation Manager to do it for you). In one of these checks, the following event was found:
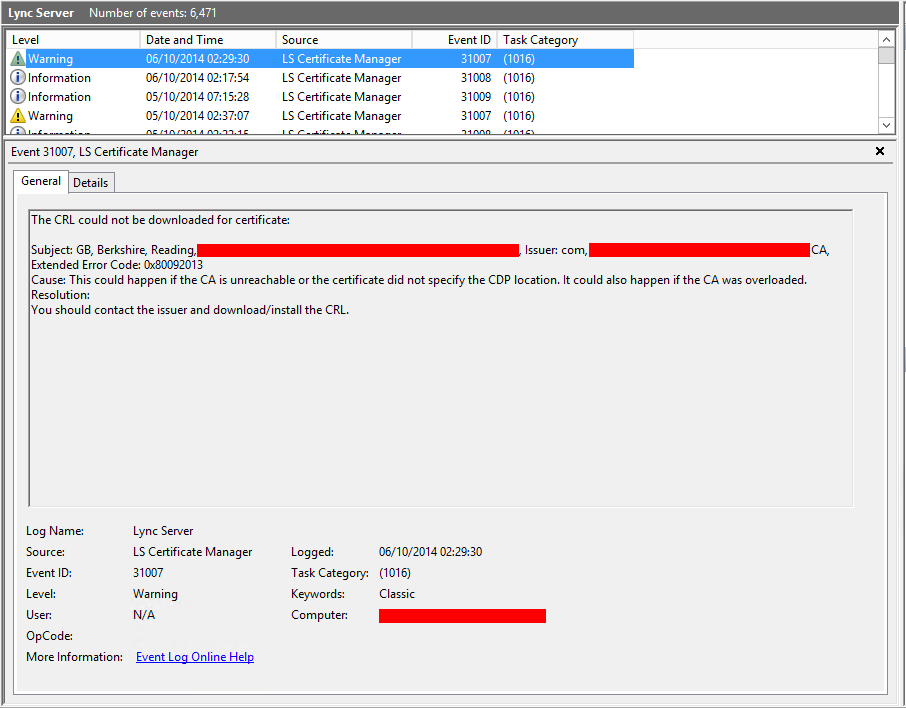
Log Name: Lync Server
Source: LS Certificate Manager
Date: 06/10/2014 02:29:30
Event ID: 31007
Task Category: (1016)
Level: Warning
Keywords: Classic
User: N/A
Computer: ******
Description:
The CRL could not be downloaded for certificate:
Subject: GB, Berkshire, Reading, ******, Issuer: com, *****, Internal-CA, Extended Error Code: 0x80092013
Cause: This could happen if the CA is unreachable or the certificate did not specify the CDP location. It could also happen if the CA was overloaded.
Resolution:
You should contact the issuer and download/install the CRL.
This event mentions that Lync Server Edge couldn’t reach CRL Distribution Points (CDP) and download the latest CRL. We didn’t notice any Lync feature affected by it, but since Lync Server relies on certificates we decided to investigate it a little further.
CRL stands for Certificate Revocation List and contains all the certificates serial numbers which were revoked by this CA. This allows the certificate to be revoked within its valid period – for example, when we need to change the Subject Alternative Names (SAN), the old certificate serial number will be included in this list.
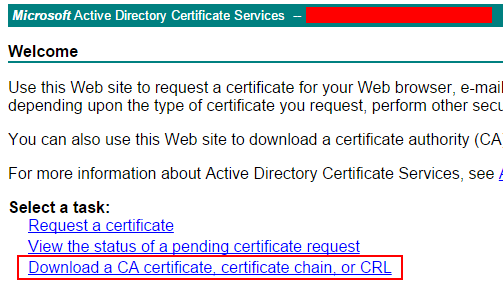
We could download the CRL from the CA and install it on the Lync Server Edge. In order to download the CRL, access http://CA-FQDN/certsrv, where there should be an option to download the current CRL:
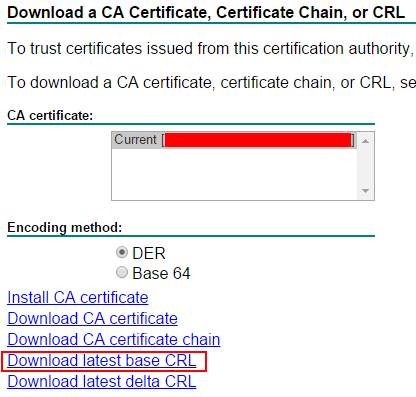
This approach isn’t so practical, since the CRL are only valid for a short period:
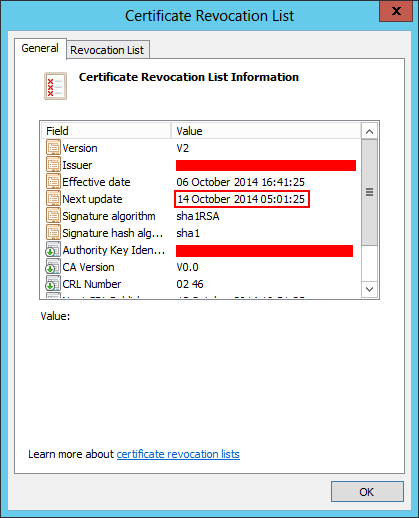
Checking the certificate CRL Distribution Points, we noticed that it only had LDAP entries:
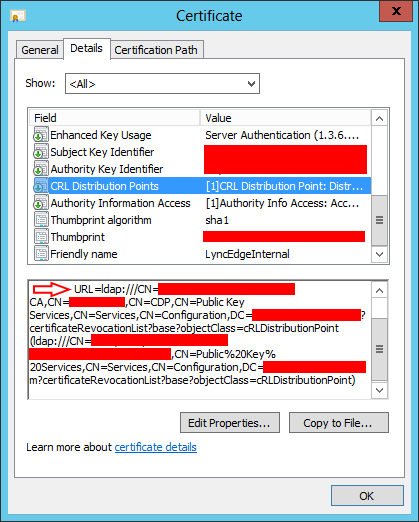
This means that our CA only had LDAP enabled for CDP. This is the default configuration when we install Active Directory Certificate Services.
The best option is to add the HTTP as CRL Distribution Point, which will allow non-domain joined computers to download the CRL. To add this, we need to access our CA and open the Certification management console.
Now, select the CA, then right click and select Properties:
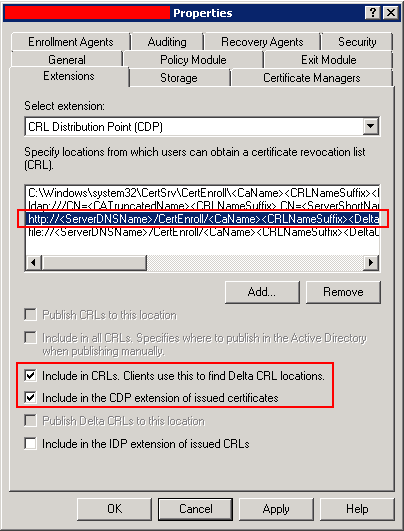
In Properties, go to Extensions tab. Enable the following option:
Include in CRLs. Clients use this to find Delta CRL locations.
Include in the CDP extension of issued certificates.
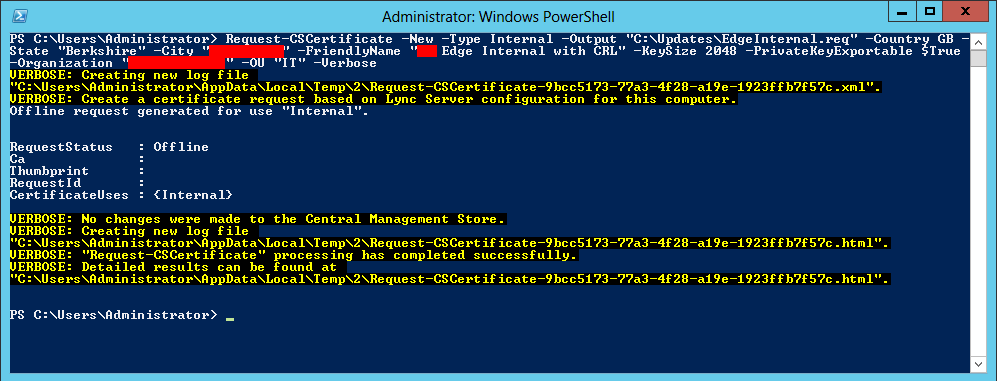
After changing and restarting the CA services, we need to update the edge certificate. Only new certificates will contain the HTTP as CDP.
Coming back to the Edge Server, we can use the Lync Deployment Wizard or PowerShell:
Request-CSCertificate -New -Type Internal -Output “C:\Certs\EdgeInternal.req” -Country GB -State “Berkshire” -City “Bracknell” -FriendlyName “Edge Internal with CRL” -KeySize 2048 -PrivateKeyExportable $True -Organization “UC Lobby” -OU “IT” -Verbose
Now, if we return to the CA, we can access http://CA-FQDN/certsrv or use the Command Prompt:
Certreq.exe –submit –attrib “CertificateTemplate:webserver” C:\Certs\EdgeInternal.req EdgeInternal.cer
We can also check if this new certificate includes HTTP CRL URL:
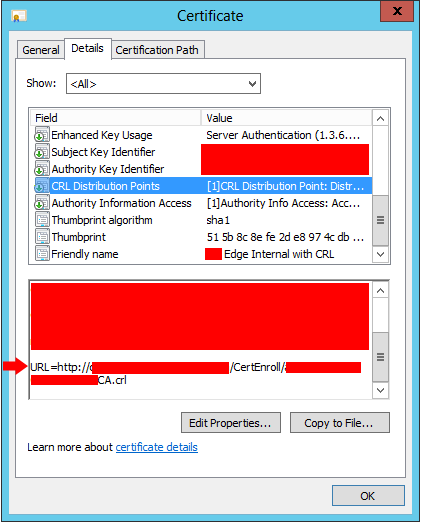
Copy the EdgeInternal.cer file to the Edge and import and assign the certificate using PowerShell:
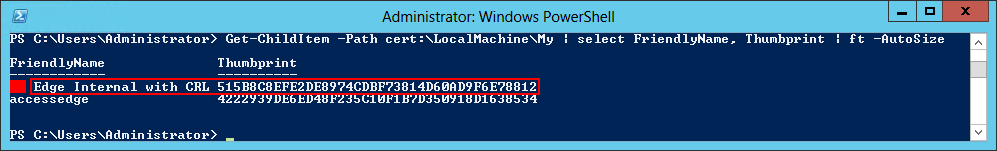
Import-CsCertificate -Path “C:\Certs\EdgeInternal.cer” -PrivateKeyExportable $True
Get-ChildItem -Path cert:\LocalMachine\My | select Subject, FriendlyName, Thumbprint | Format-List
Set-CsCertificate -Type Internal -Thumbprint <Certificate Thumbprint>
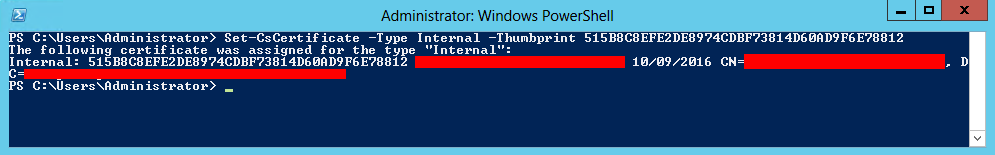
After assigning the new certificate, we won’t get Event 31007 in the Event Viewer. Please take into consideration that the Certificate Manager only checks the certificates twice per day.