In case we delete, by mistake, a certificate using the Certificate snap-in, we can still restore it. In order to do this, we need to import the certificate again and reassign the stored private key to it, without having to create a new request.
The following article was published for IIS, but it also applies to Lync/SfB Server and to Exchange Server:
How to assign a private key to a new certificate after you use the Certificates snap-in to delete the original certificate in Internet Information Services
https://support.microsoft.com/kb/889651
The first step is to import the certificate again to the Computer Personal Store:
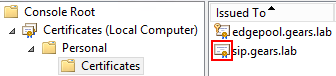
After importing the certificate, if it doesn’t have the private key assigned, we cannot use the certificate in any Lync/SfB Server service.
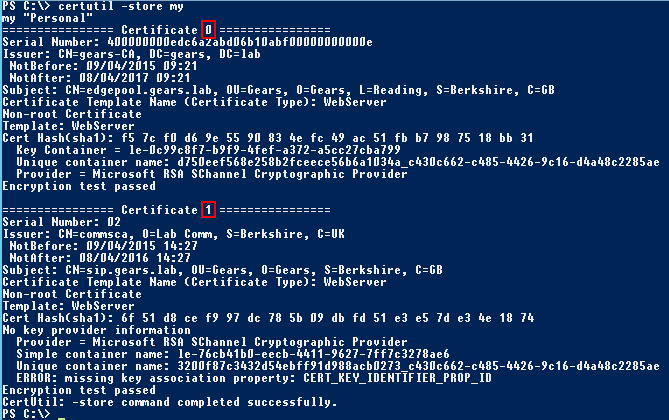
Now we need to take note of the certificate Serial Number. We can get it either in the certificate Details tab:
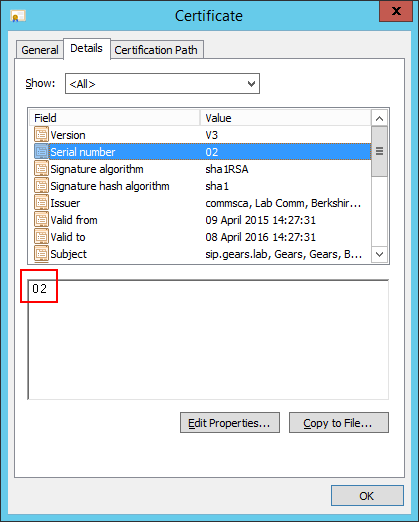
Note: This is a lab CA and that is why the serial number is just 02, because normally you will have something like 04 3b df f8 25 84 cd. This serial number is given by the CA and it is the Serial Number that will be included in the CRL if the certificate is revoked.
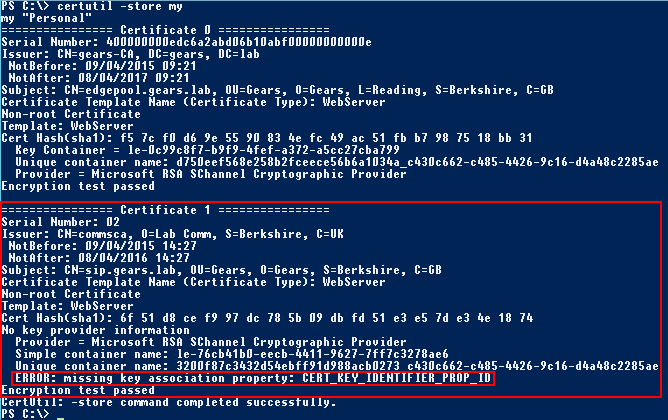
Or use the Certutil store switch:
certutil -store my
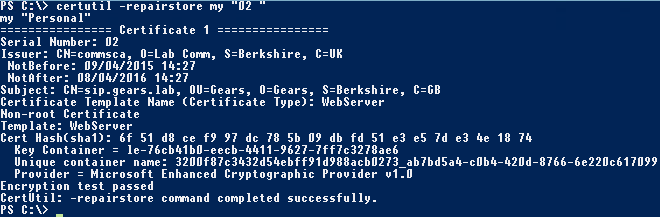
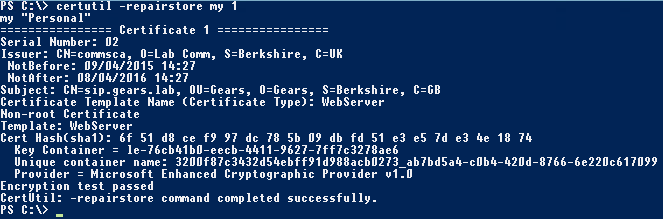
In a Command Prompt/PowerShell, we run the certutil with the repairstore switch:
certutil -repairstore my “Serial Number“
Alternatively, we can use the certificate index in the store. The index number is returned by the certutil -store my command:
certutil -repairstore my 1
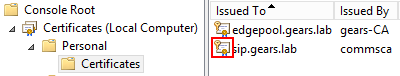
If the private key is successfully assigned, we will see it in the Computer Personal Store after refreshing it:
Please note that sometimes the private key is lost and we will have to create a new request.
This method will also work if we change Certificate Common Name or add/remove FQDN to the SAN. In this case, we need to follow these steps:
- Request the changes in the Certificate Authority online website (note that if we re-key the certificate, we need to import the certificate as usual);
- Download the certificate;
- Import the certificate to the server;
- Take note of the certificate Serial Number;
- Run certutil -repairstore my “Serial number”